Issue
This has been one of the most embarrassing issues in quite some time. Issue was, that my MS Outlook 2016 (connected to an Exchange Online Plan / Microsoft 365) kept asking for a password, but the dialogue window disappeared immediately with no chance of entering a password. In effect, Outlook was not able to connect to the Exchange server, so that no emails could be sent nor received.
Options that didn’t work
(yet may be helpful in other cases)
When googling for the issue, I ended up with some comprehensive forum posts and lists of potential solutions [1, 2], but nothing of the below worked (even though it may work in other situations):
- Repair-Install / Online Repair Office 365
- Delete Outlook Account(s) and re-add them
- Delete Email Profile from Windows 10 Settings, and create a new one (all accounts get deleted in the process and have to be set up again afterwards!)
- Some advanced repair options listed here (some connected to Modern Auth)
- Checking my Domain DNS settings (for some advanced analysis and troubleshooting, the MS tools Support and Recovery Assistant and the Microsoft Remote Connectivity Analyzer turned out to be very helpful)
Solution
It turned out that the root cause was different than what I expected. I had previously updated my BIOS, and during the process it also updated the TPM (Trusted Platform Module) settings of my AMD x570 based PC. The TPM is a dedicated chip (or on AMD platforms mostly a virtualized component) which safely stores encryption keys for i.e. Bitlocker and other security applications on a hardware level. It turns out, that updating the BIOS had reset the TPM and deleted all the stored keys which it held. Also Microsoft accounts for both, Windows and Office 365 seem to store some keys there which had been affected in my case.
Windows 10 still had the Exchange account listed with no issues under Settings > Accounts, but in fact -due to a missing TPM key- it was not able to access the account properly (without noticing the user btw).
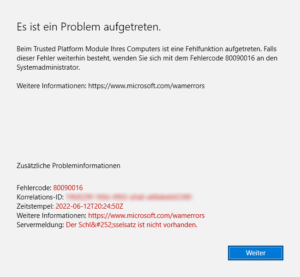
Finally, when I tried to delete the Exchange Account from Settings > Accounts > Access Business & School Accounts, it gave me this error message (Error 80090016):
Please note that you must perform this action in both places, under Accounts > Email and Accounts and under Access Business and School Accounts! Only after removing the Exchange account from the second option will really and finally remove the account from Windows.
After clicking on the button, it finally removed the account, and after logging back into the same account (after rebooting), everything worked again. Having tried all the above things before, I had to reconfigure all my Exchange accounts and Outlook settings, but logging off and on again should spare you all of that, just give it a try. Luckily I had a recent backup which saved me hours of work.
PS: Having a full Outlook backup in place is a great thing, including all the PST files, but also all configuration settings, signatures etc. The best tool I found for this (using it for 10+ years now) is MObackup. (No I am not affiliated with the creator, nor do I get any incentive or kickback, I am just a very convinced user for years).